2024"观安杯"ISG WP
2024年国家网络安全宣传周上海地区活动 "观安杯"ISG网络安全管理运维赛WP
题名:misc_office
题下载下来后直接打开发现被加密了,密码不知道
右键->详细信息->备注可以看到密文:SSN6aVR4bnh2YmcjR0M5
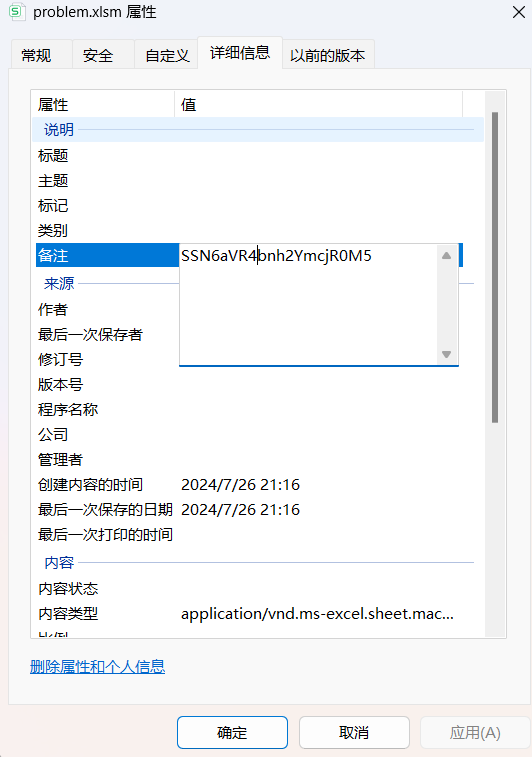 Base64解密后得到密码:I#ziTxnxvbg#GC9
Base64解密后得到密码:I#ziTxnxvbg#GC9 可以解开表
可以解开表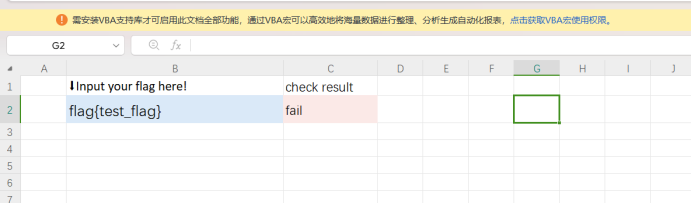 打开表可以看到有VBA宏,猜测里面肯定有东西,这里使用oletools工具里的olevba.py
打开表可以看到有VBA宏,猜测里面肯定有东西,这里使用oletools工具里的olevba.py
工具地址:https://pypi.org/project/oletools/#files
命令:python olevba.py .\problem.xlsm -p I#ziTxnxvbg#GC9
得到代码: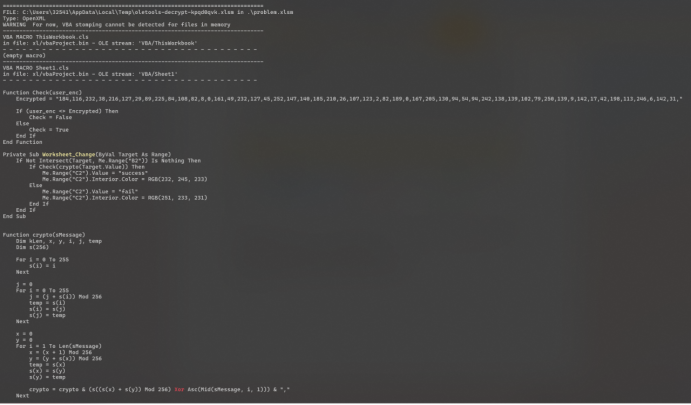 详细信息:
详细信息:
Function Check(user_enc)
Encrypted = "184,116,232,38,216,127,29,89,225,84,108,82,8,0,161,49,232,127,45,252,147,140,185,210,26,107,123,2,82,189,0,167,205,130,94,54,94,242,138,139,102,79,250,139,9,142,17,42,198,113,246,6,142,31,"
If (user_enc <> Encrypted) Then
Check = False
Else
Check = True
End If
End Function
Private Sub Worksheet_Change(ByVal Target As Range)
If Not Intersect(Target, Me.Range("B2")) Is Nothing Then
If Check(crypto(Target.Value)) Then
Me.Range("C2").Value = "success"
Me.Range("C2").Interior.Color = RGB(232, 245, 233)
Else
Me.Range("C2").Value = "fail"
Me.Range("C2").Interior.Color = RGB(251, 233, 231)
End If
End If
End Sub
Function crypto(sMessage)
Dim kLen, x, y, i, j, temp
Dim s(256)
For i = 0 To 255
s(i) = i
Next
j = 0
For i = 0 To 255
j = (j + s(i)) Mod 256
temp = s(i)
s(i) = s(j)
s(j) = temp
Next
x = 0
y = 0
For i = 1 To Len(sMessage)
x = (x + 1) Mod 256
y = (y + s(x)) Mod 256
temp = s(x)
s(x) = s(y)
s(y) = temp
crypto = crypto & (s((s(x) + s(y)) Mod 256) Xor Asc(Mid(sMessage, i, 1))) & ","
Next
分析可知是个对称的rc4异或加密。编写解密脚本:
liuut=[184,116,232,38,216,127,29,89,225,84,108,82,8,0,161,49,232,127,45,252,147,140,185,210,26,107,123,2,82,189,0,167,205,130,94,54,94,242,138,139,102,79,250,139,9,142,17,42,198,113,246,6,142,31]
git = []
uu = [x for x in range(0x100)]
k = 0
for i in range(0x100):
k = (k+uu[i])%0x100
tmp = uu[i]
uu[i] = uu[k]
uu[k] = tmp
x = 0
y = 0
for i in liuut:
x = (x+1)%0x100
y = (y+uu[x])%0x100
tmp = uu[x]
uu[x] = uu[y]
uu[y] = tmp
git.append(chr(i^uu[(uu[x]+uu[y])%0x100]))
print(''.join(git))
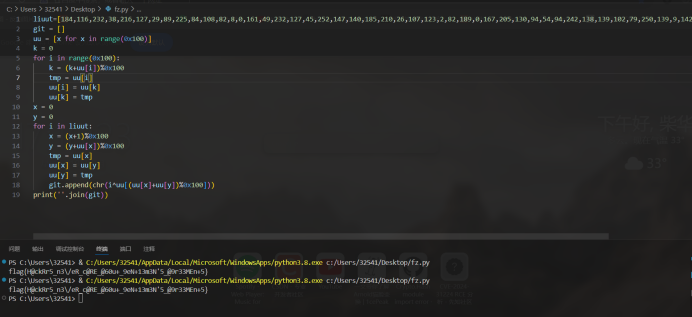 得到flag
得到flag
flag{H@ckRr5_n3/eR_c@RE_@60u+9eN+13m3N'5@9r33MEn+5}
题名:misc_see_it
题下载下来是一个音频文件
 使用binwalk分析一下
使用binwalk分析一下
命令:binwalk challenge.wav --run-as=root
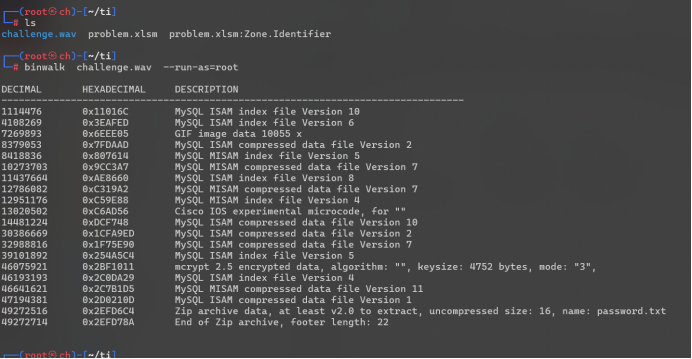
可以看到有内容:一个password.txt里面有密码
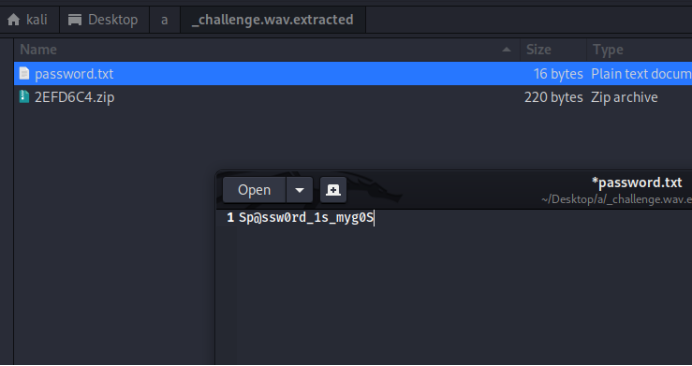 得到密码
得到密码
看视频的16进制有steghide的字样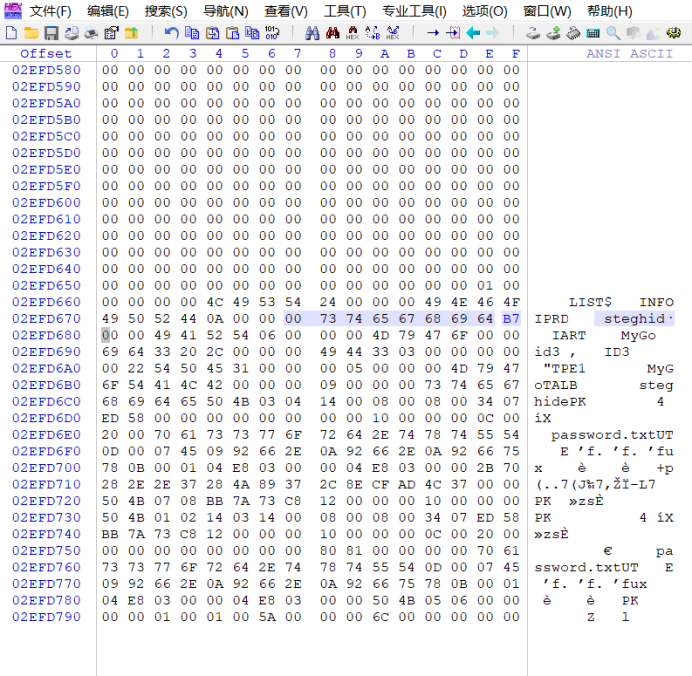 使用命令:steghide extract -sf challenge.wav -p p@ssw0rd_1s_myg0分以下得到图片:
使用命令:steghide extract -sf challenge.wav -p p@ssw0rd_1s_myg0分以下得到图片: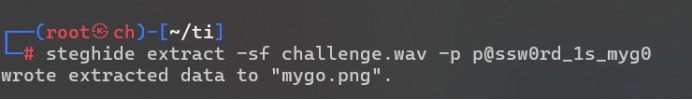
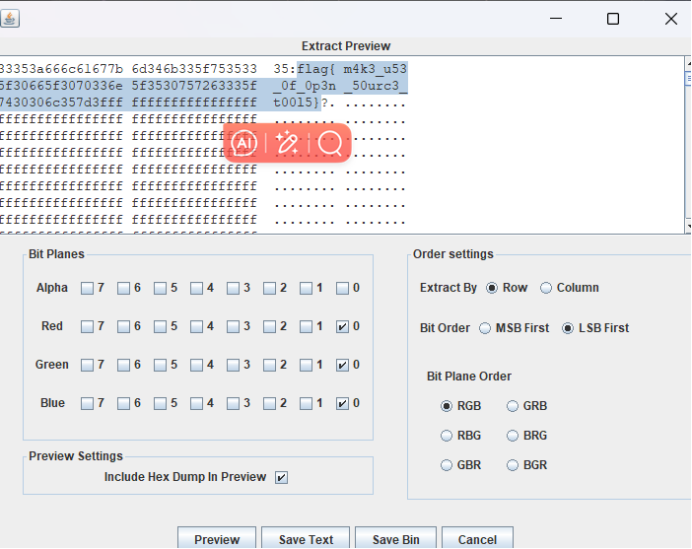
 解lsb色道隐写得到flag(这里解lsb色道隐写使用的是Stegsolve)
解lsb色道隐写得到flag(这里解lsb色道隐写使用的是Stegsolve)
题名:web_emm
题目打开后随便注册一个管理员用户,安装后进入后台
 看到插件那一栏可以自己导入插件,猜测是安装插件get shell
看到插件那一栏可以自己导入插件,猜测是安装插件get shell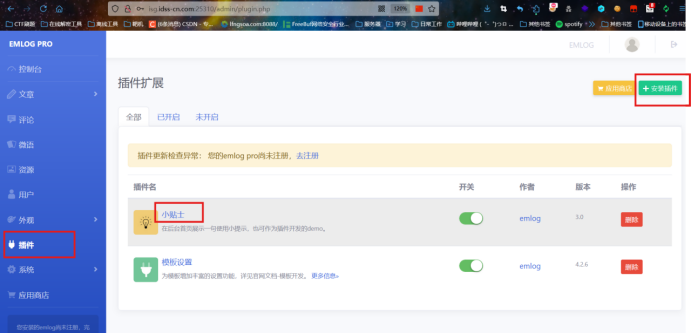 先删除小贴士插件然后下载Emlog-Pro-getshell
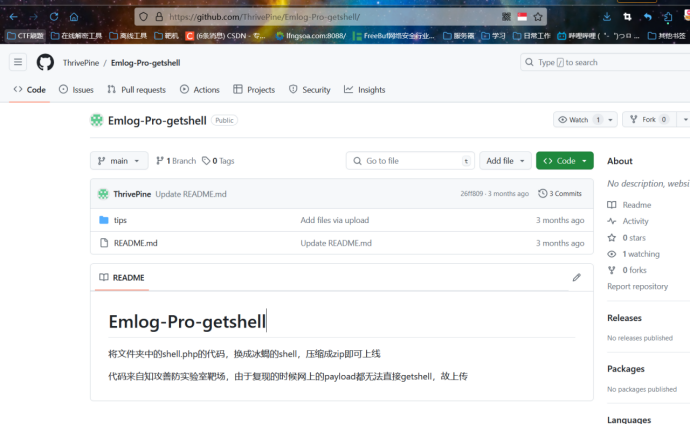
先删除小贴士插件然后下载Emlog-Pro-getshell
插件地址:https://github.com/ThrivePine/Emlog-Pro-getshell/
 下载后进入tips文件夹把shell.php给添加一句话木马
下载后进入tips文件夹把shell.php给添加一句话木马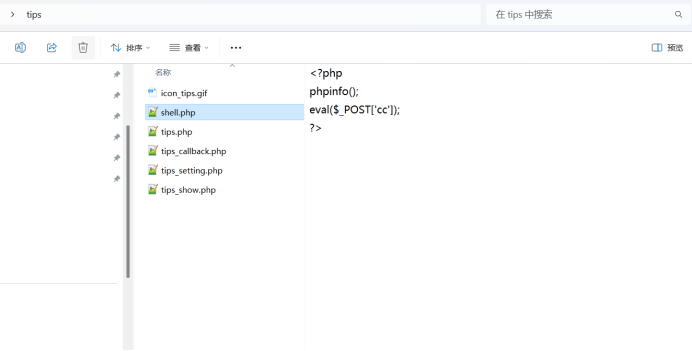 后将tips文件夹打成压缩包后在安装插件处上传
后将tips文件夹打成压缩包后在安装插件处上传
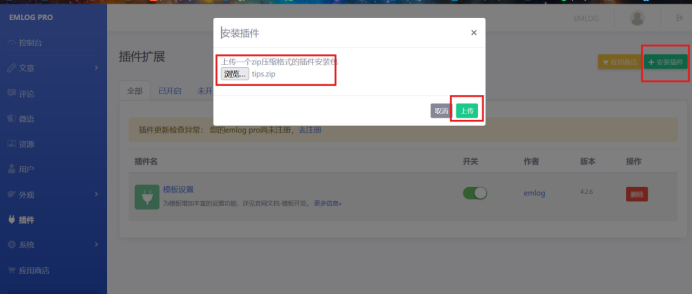 开启插件
开启插件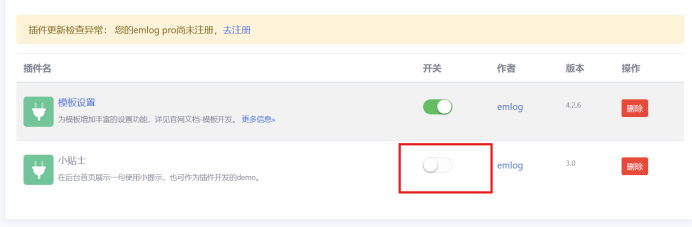 开启插件,后访问/content/plugins/tips/shell.php
开启插件,后访问/content/plugins/tips/shell.php 之后post传参cc=system('cat /flag');得到flag
之后post传参cc=system('cat /flag');得到flag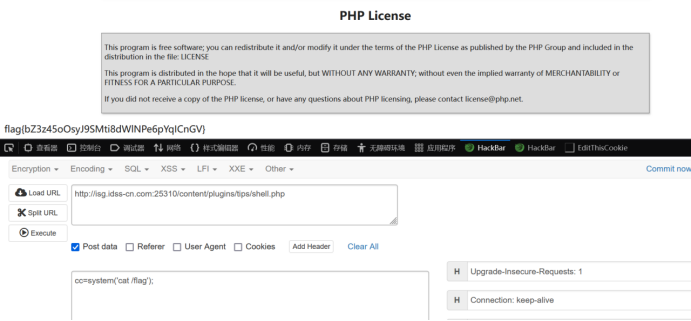 flag{bZ3z45oOsyJ9SMti8dWlNPe6pYqICnGV}
flag{bZ3z45oOsyJ9SMti8dWlNPe6pYqICnGV}

