2024年全国大学生信息安全竞赛安徽省赛(线上初赛)-本科组WP
MISC:
题名:你是黑客么
拿到题目压缩包后通过密码爆破得到密码:
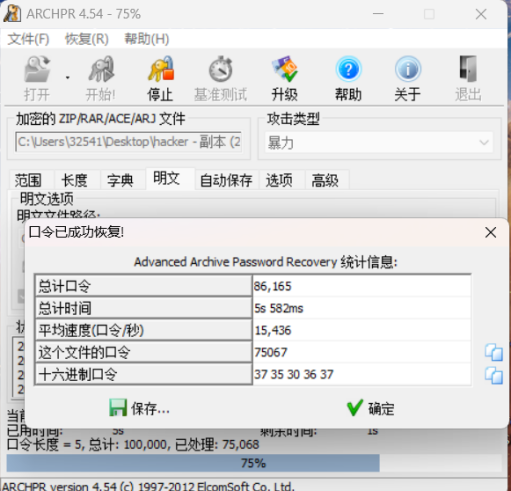
通过解压压缩包获得1.jpg,使用010看图片最底部发现base64加密的图片数据:
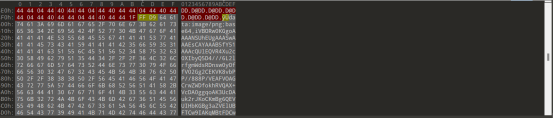
使用工具解压缩base64获得图片后
得到二维码:

扫描二维码得到flag
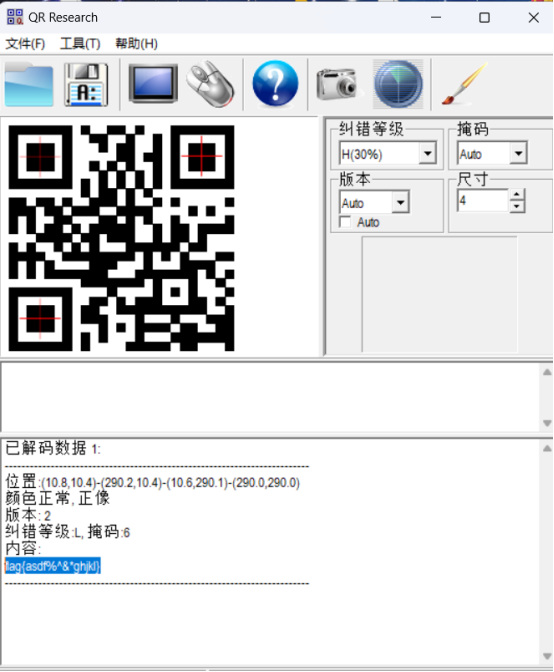
Flag:
flag{asdf%^&*ghjkl}
题名:九连环
拿到题目压缩包后解开有张名为123456cry.jpg的图片:

使用binwalk分离得到压缩包
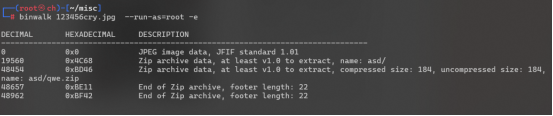
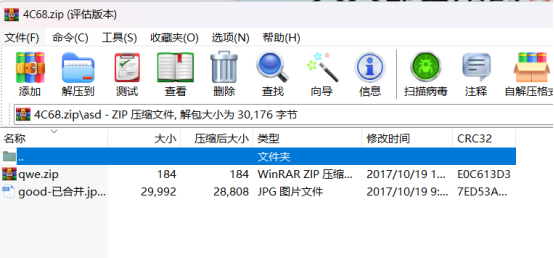
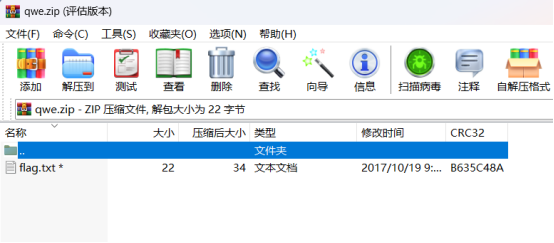
qwe压缩包可以直接解压里面有flag.txt,但是good-已合并.jpg需要密码
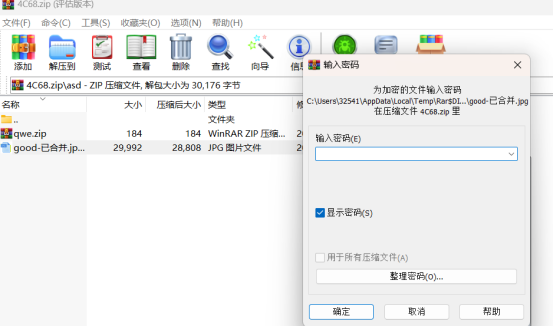
通过zip伪加密提取出good-已合并.jpg:

发现是是jpg隐写使用工具 steghide
steghide extract -sf good-已合并.jpg
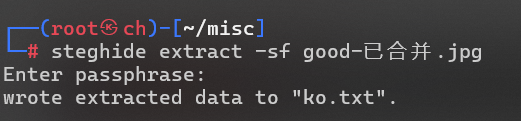
得到ko.txt
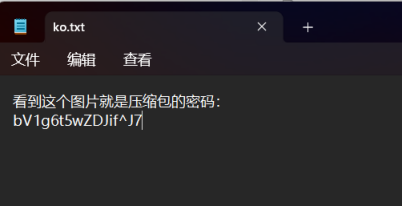
bV1g6t5wZDJif^J7
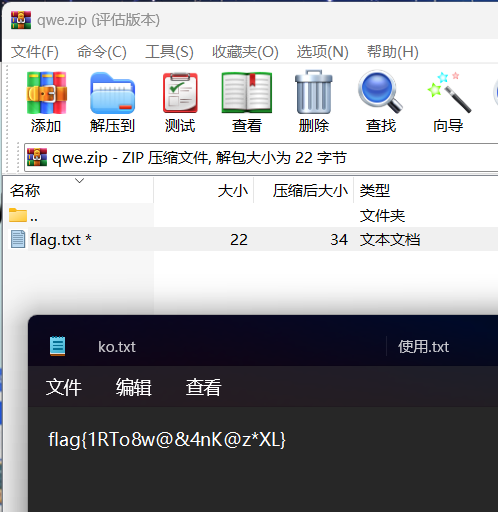 使用密码解压qwe.zip得到flag
使用密码解压qwe.zip得到flag
Flag:
flag{1RTo8w@&4nK@z*XL}
题名:Forgotten password
打开题目是一个内存镜像,放工具里分析一下
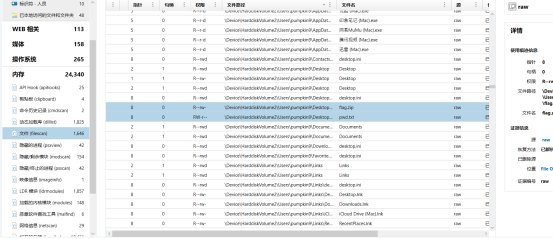
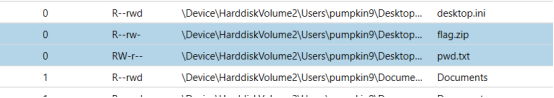
看到桌面上有疑似文件
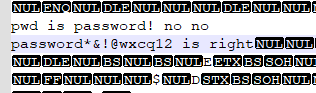
提取出来后看pwd.txt,得到密码:
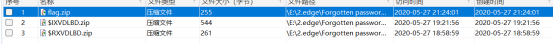
然后使用密码提取flag.zip,解压得到flag.txt
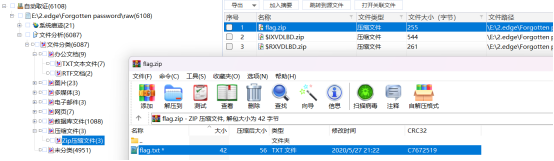
Flag:
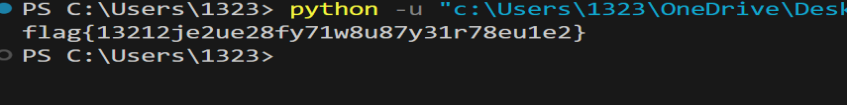
flag{4e0fcb08-48bd-4b70-99c3-a6a029c5e105}
密码
题目:Rsa_roll
题目给了n,e 和多组c
所以先分解n
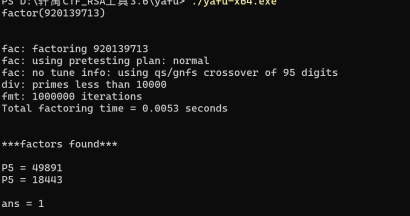
然后就是把每一组的c都去解m然后转字符拼接在一起
EXP:
from gmpy2 import*
from Crypto.Util.number import*
n,e={920139713,19}
p = 49891
q = 18443
d=invert(e,(p-1)*(q-1))
c=(704796792,
752211152,
274704164,
18414022,
368270835,
483295235,
263072905,
459788476,
483295235,
459788476,
663551792,
475206804,
459788476,
428313374,
475206804,
459788476,
425392137,
704796792,
458265677,
341524652,
483295235,
534149509,
425392137,
428313374,
425392137,
341524652,
458265677,
263072905,
483295235,
828509797,
341524652,
425392137,
475206804,
428313374,
483295235,
475206804,
459788476,
306220148)
flag=''
for i in c:
m=pow(i,d,n)
a=long_to_bytes(m)
flag+=a.decode()
print(flag)
Ras_gcd
通过题目·给的数据发现是共享素数题型,直接gcd(n1,n2)知道p,然后正常·c1,c2解rsa,拼在一起
Exp
from gmpy2 import*
from Crypto.Util.number import*
n1=23220619839642624127208804329329079289273497927351564011985292026254914394833691542552890810511751239656361686073628273309390314881604580204429708461587512500636158161303419916259271078173864800267063540526943181173708108324471815782985626723198144643256432774984884880698594364583949485749575467318173034467846143380574145455195152793742611717169602237969286580028662721065495380192815175057945420182742366791661416822623915523868590710387635935179876275147056396018527260488459333051132720558953142984038635223793992651637708150494964785475065404568844039983381403909341302098773533325080910057845573898984314246089
e=65537
c1=9700614748413503291260966231863562117502096284616216707445276355274869086619796527618473213422509996843430296526594113572675840559345077344419098900818709577642324900405582499683604786981144099878021784567540654040833912063141709913653416394888766281465200682852378794478801329251224801006820925858507273130504236563822120838520746270280731121442839412258397191963036040553539697846535038841541209050503061001070909725806574230090246041891486506980939294245537252610944799573920844235221096956391095716111629998594075762507345430945523492775915790828078000453705320783486744734994213028476446922815870053311973844961
n2=22642739016943309717184794898017950186520467348317322177556419830195164079827782890660385734113396507640392461790899249329899658620250506845740531699023854206947331021605746078358967885852989786535093914459120629747240179425838485974008209140597947135295304382318570454491064938082423309363452665886141604328435366646426917928023608108470382196753292656828513681562077468846105122812084765257799070754405638149508107463233633350462138751758913036373169668828888213323429656344812014480962916088695910177763839393954730732312224100718431146133548897031060554005592930347226526561939922660855047026581292571487960929911
e=65537
c2=20513108670823938405207629835395350087127287494963553421797351726233221750526355985253069487753150978011340115173042210284965521215128799369083065796356395285905154260709263197195828765397189267866348946188652752076472172155755940282615212228370367042435203584159326078238921502151083768908742480756781277358357734545694917591921150127540286087770229112383605858821811640935475859936319249757754722093551370392083736485637225052738864742947137890363135709796410008845576985297696922681043649916650599349320818901512835007050425460872675857974069927846620905981374869166202896905600343223640296138423898703137236463508
p=gcd(n1,n2)
q1=n1//p
phi1=(p-1)*(q1-1)
d1=invert(e,phi1)
q2=n2//p
phi2=(p-1)*(q2-1)
d2=invert(e,phi2)
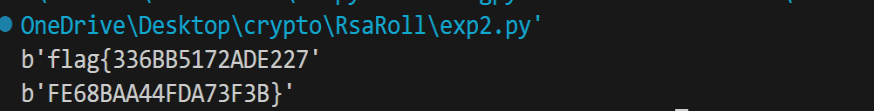
print(long_to_bytes(pow(c1,d1,n1)))
print(long_to_bytes(pow(c2,d2,n2)))
Easycrypt
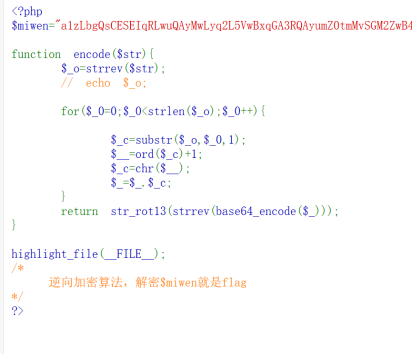
就是通过·理解原码逆向解密 先解rot13在反转再解base64,在反转,遍历每个字符并将其ASCII值减一,然后转换回字符。
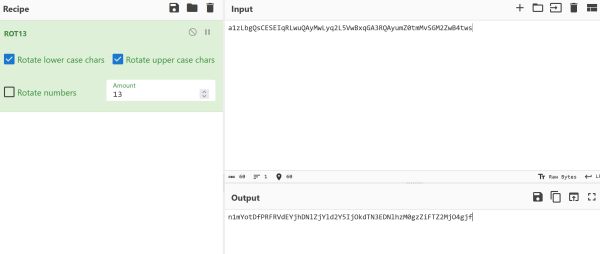
import base64
a='n1mYotDfPRFRVdEYjhDNlZjYld2Y5IjOkdTN3EDNlhzM0gzZiFTZ2MjO4gjf'
b=base64.b64decode(a[::-1])
c=b[::-1]
for i in c.decode():
print(chr(ord(i)-1),end='')
Reverse
题名:Nuaactf
解压附件得到一个jar文件,用jadx反编译
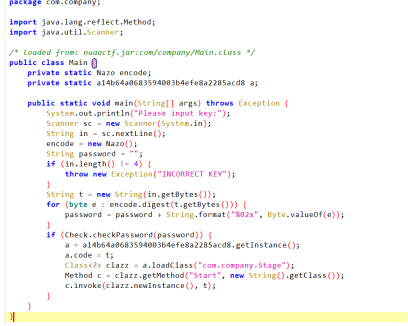
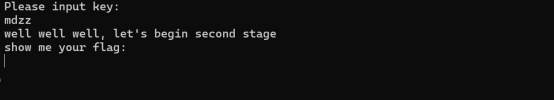
观察主函数,发现在主函数中密码为四位,进行爆破得出密码mdzz
import string ,hashlib,
for i in string.printable:
for j in string.printable:
for k in string.printable:
for l in string.printable:
if hashlib.sha1((i+j+k+l).encode('utf-8')).hexdigest() == "caf4cbafdf72ce0f2f2eadc4309916e8c96f0de8":
return i+j+k+l
主函数通过a14b64a0683594003b4efe8a2285acd8 类来载入其他类执行方法,
将传入的最后一个类名,也就是当前类名取出,将类名md5加密,重新形成新的包,接下来将当前包进行AES解密,iv为****************,key为mdzz
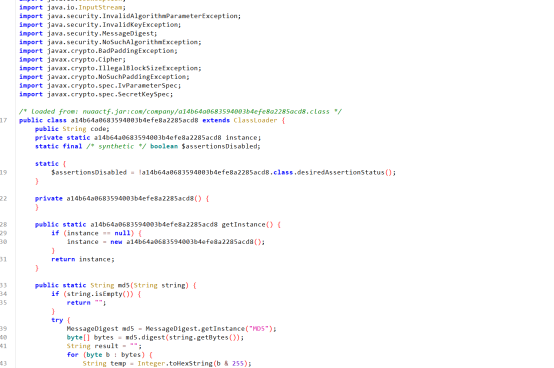
利用脚本将类解密
import java.io.*;
import javax.crypto.spec.SecretKeySpec;
import java.security.InvalidAlgorithmParameterException;
import java.security.InvalidKeyException;
import javax.crypto.BadPaddingException;
import javax.crypto.Cipher;
import javax.crypto.IllegalBlockSizeException;
import javax.crypto.NoSuchPaddingException;
import javax.crypto.spec.IvParameterSpec;
import java.security.MessageDigest;
import java.security.NoSuchAlgorithmException;
/**
* Created by link on 2017/10/1.
*/
public class Decode {
private static String code = "mdzz";
public static String md5(String string)
{
if (string.isEmpty()) {
return "";
}
MessageDigest md5 = null;
tr
{
md5 = MessageDigest.getInstance("MD5");
byte[] bytes = md5.digest(string.getBytes());
String result = "";
for (byte b : bytes)
{
String temp = Integer.toHexString(b & 0xFF);
if (temp.length() == 1) {
temp = "0" + temp;
}
result = result + temp;
}
return result;
}
catch (NoSuchAlgorithmException e)
{
e.printStackTrace();
}
return "";
}
public static void decodeClass(String name)
{
// File file = new File(name);
InputStream in = null;
FileOutputStream out = null;
try {
in = new FileInputStream(name);
out = new FileOutputStream(name + "_decode.class");
} catch (FileNotFoundException e) {
e.printStackTrace();
}
long len = 0L;
try
{
len = in.available();
}
catch (IOException e)
{
e.printStackTrace();
}
byte[] raw = new byte[(int)len];
int off = 0;int rst = 0;
try
{
for (;;)
{
rst = in.read(raw, off, (int)len);
if (rst == len) {
break;
}
off += rst;
len -= rst;
}
}
catch (IOException e)
{
e.printStackTrace();
}
String ivStr = "****************";
MessageDigest md = null;
try
{
md = MessageDigest.getInstance("MD5");
}
catch (NoSuchAlgorithmException e)
{
e.printStackTrace();
}
assert (md != null);
md.update(code.getBytes());
byte[] key = md.digest();
Cipher AES = null;
try
{
}
catch (NoSuchAlgorithmException e)
{
e.printStackTrace();
}
catch (NoSuchPaddingException e)
{
e.printStackTrace();
}
SecretKeySpec spec = new SecretKeySpec(key, "AES");
IvParameterSpec iv = new IvParameterSpec(ivStr.getBytes());
try
{
assert (AES != null);
}
catch (InvalidAlgorithmParameterException e)
{
e.printStackTrace();
}
catch (InvalidKeyException e)
{
e.printStackTrace();
}
byte[] en = null;
try
{
en = AES.doFinal(raw);
}
catch (BadPaddingException e)
{
e.printStackTrace();
}
catch (IllegalBlockSizeException e) {
e.printStackTrace();
}
try {
out.write(en);
out.close();
} catch (IOException e) {
e.printStackTrace();
}
}
public static void main(String argv[]){
String filename = FilePath;
for(int i = 2; i <= 8; i++){
decodeClass(filename + md5(String.format("Stage%d", i)) + ".class");
}
return ;
}
}
观察加密流程
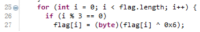
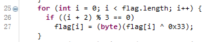
编写python脚本进行解密
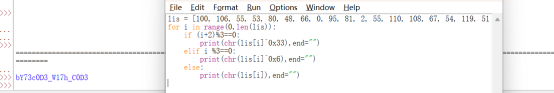
Flag:
nuaactf{ bY73c0D3_W17h_C0D3}
题名:Reverse400
先用pyinstxtractor进行解包,将解包得出的Reverse03.pyc直接打开
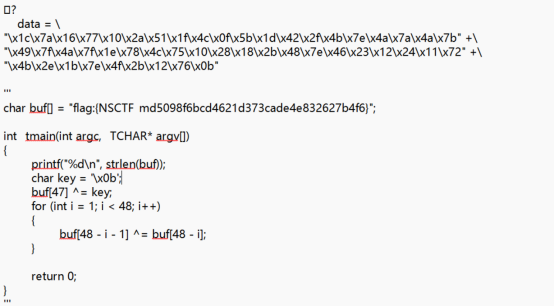
利用python解密
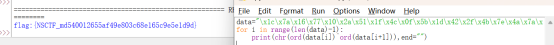
Flag:
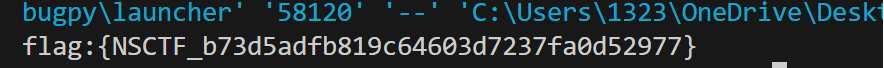
flag{NSCTF_md540012655af49e803c68e165c9e5e1d9d}
题名:Crackme
IDA打开exe, shift f12
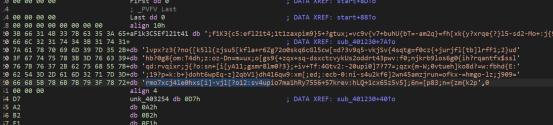
得到一个串字符疑似密文
打开exe,随便输入出了一个报错的对话框
找到调用MESSAGE的函数,判断flag
发现sub_4016E0、sub_401720都调用了MESSAGE
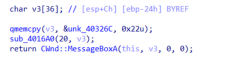
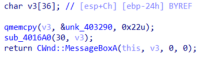
sub4015E0调用了两个函数

接着去查看sub_401630函数发现加密过程
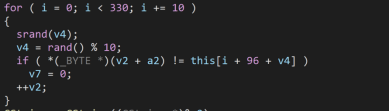
利用python进行解密
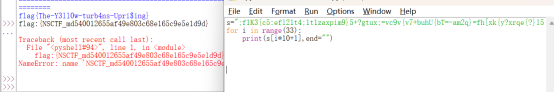
得到flag:
Flag:
flag{The-Y3ll0w-turb4ns-Upri$ing}